I)ruid has been bringing challenges and puzzles to DEF CON himself for over two decades, and under the Rogue Signal brand for nearly half of that time. This year, for DEF CON 30, we significantly upped our game by building and branding a custom Scramble! game interface that we’ve dubbed “Hac-Man“.
To get Players started, we printed and distributed 5000 Hac-Man invite cards around the conference, as well as posted the image shown above to social media.
Hac-Man is a Pac-Man styled set of game boards that takes the Player, represented by Hac-Man, through a bunch of mazes chomping on pellets, fruit, power-pellets, and ghosts. Everything that Hac-Man could eat would award a specific number of points and provides a different game mechanic.
Each ghost on the game board represents a unique and individual puzzle or challenge, and each maze represents a track or collection of puzzles and challenges. There are two types of mazes, “linear completion” or “Track” mazes and “non-linear completion” or “Group” mazes:


In linear mazes, as the name implies, the Player’s Hac-Man can only move through the maze along one pre-determined path, and must complete each challenge ghost before being able to access and attempt the next. In non-linear mazes, Hac-Man could access most of, if not all, the challenge ghosts from anywhere in the maze, allowing the Player to pick and choose the challenges they attempted from the entire collection.
To complete a linear maze, Hac-Man would need to complete all of the included challenges, whereas in each non-linear maze, the Player’s progress would have been deemed “complete” at a particular points threshold for the maze, not requiring 100% completion of all tasks. Because each maze totals 300 points, and each challenge ghost awarded a different percentage of that total, reaching “completion” for a non-linear maze could be accomplished through multiple possible combinations of completed challenge ghosts.
Collecting fruit allowed the player to then “spend” the fruit to unlock hints about individual challenges, including a text hint and location information.
The overall winners of our DEF CON Hac-Man challenge are determined by the points Leaderboard, and this year we gave away some pretty amazing prizes for the Top Ten players on the leaderboard when the game concluded, including most major video game consoles as well as a number of Steam gift cards:

The overall game itself had 81 individual puzzles and challenges, and as this post is intended to be more of an overview, we don’t want to cover every single challenge here, so we’ll hit some of the highlights. You can however find a full walk-through of each individual challenge over on PrestonZen’s blog.
Qualifier Track
The game begins after a Player registers with our “Scramble!” game platform, creating a user account. Upon registering, the Player was presented with a “Track” maze for the Qualifier Track. The Qualifier Track was intended to be a set of challenges representing some basic technology and hacker skills that the player would need to pass to make it to our “Lobby Maze”.
In the Qualifier Track, we had some basic challenges representing skills like joining our community Discord server, hashing some data using SHA-256, viewing the source code and robots.txt file of a website, some PGP related skills, and digging around in DNS records. We won’t bore you too much with going into detail on these challenges, as they really were fairly basic. Most of the Players that got stuck on the Qualifier Track did so at the PGP challenges.
Lobby Maze
After completing the Qualifier Track, the Player progressed to our “Lobby Maze”, a maze where there were a number of tunnels leading off the left and right sides of the maze to a handful of subject-matter specific Tracks, the Leaderboard, the Player’s personal QR code, and our Hac-Man T-Shirt Shop.

In this maze there was also fruit that would spawn near the center, which Players could collect and spend to unlock hint and location information about individual challenges. The fruit were worth 5 points each, and would respawn 30 minutes after being last eaten, so a Player could potentially rack up some extra bonus points from diligently eating fruit shortly after it respawned each time.
Finally, at the top of this maze was a locked door, leading to the Final Track of challenges, which would remain locked until the Player had completed at least one of the other subject-matter specific tracks.
Ciphers Track
Everyone loves ciphers and codes, right? We felt that we definitely needed to have a full track of cipher challenges for any good hacker game, so we came up with 10 progressively more difficult ciphers for this linear completion maze.
Starting off with a fairly trivial Caesar Cipher, this track quickly progressed in difficulty, even including two brand-new ciphers created by I)ruid, his SpongeMock and Astrology ciphers. Another couple of interesting ciphers from Zonkism included one with data encoded as musical notes on sheet music, and then finally a fairly difficult multi-step Enigma cipher.
SpongeMock
| Hint: | Kappa Geminorum |
| Location: | Among the Stars |
| Challenge: | who lIvEs In a piNEappLe UNDer The SEA? sPonGeBOb SQuarEPaNTs! AbSOrBeNT aNd yElloW And POroUS is HE... spONgeBOB sQUarepants! |
With the rise in popularity of the Mocking SpongeBob meme, I)ruid recognized a fairly trivial way to encode binary data in alphabetic covertext. By capitalizing letters to represent 1’s and lowercasing letters to represent 0’s, I)ruid created a simple binary encoding method where the ciphertext closely resembled the upper and lower-casing of text used in the Mocking SpongeBob memes. The ciphertext was:
who lIvEs In a piNEappLe UNDer The SEA? sPonGeBOb SQuarEPaNTs! AbSOrBeNT aNd yElloW And POroUS is HE... spONgeBOB sQUarepants!Decoded to binary using uppercase for 1 and lowercase for 0:
01010000 01100001 01110100 01110010 01101001 01100011 01101011 00101101 00110001 00110011 00110011 00110111And finally to ASCII using the less common least-significant bit first (LSB) encoding for the binary:
Patrick-1337Entering “Patrick-1337” would solve this challenge.
I)ruid’s Astrology Cipher
| Hint: | Kappa Geminorum |
| Location: | Among the Stars |
| Challenge: | ♓︎♐︎♎︎♐︎♓︎♑︎♋︎♈︎♓︎♎︎♈︎♒︎♋︎♈︎♏︎♊︎♓︎♎︎♌︎♓︎♋︎♓︎♉︎♈︎♓︎♌︎♒︎♍︎♐︎♒︎♑︎♋︎♍︎♊︎♌︎♋︎♌︎♍︎♓︎♒︎♍︎♌︎♐︎♌︎♉︎♎︎♉︎♋︎♋︎♈︎♒︎♋︎♌︎♋︎♉︎♌︎♏︎♊︎♒︎♑︎♍︎♊︎♑︎♎︎♋︎♐︎♒︎♒︎♓︎♑︎♌︎♈︎♏︎♏︎♐︎♑︎♏︎♍︎♍︎♉︎♉︎♎︎♒︎♉︎♒︎♌︎♈︎♐︎♏︎♌︎♊︎♉︎♉︎♐︎♊︎♍︎♍︎♑︎♐︎♉︎♑︎♋︎♓︎♍︎♑︎♌︎♈︎♎︎♍︎♎︎♉︎♏︎♋︎♊︎♎︎♉︎♐︎♍︎♏︎♑︎♋︎♈︎♌︎♓︎♍︎♈︎♑︎♊︎♏︎♓︎♐︎♍︎♉︎♑︎♓︎♉︎♓︎♒︎♌︎♐︎♐︎♓︎♏︎♐︎♋︎♊︎♌︎♑︎♏︎♌︎♑︎♈︎♑︎♌︎♌︎♉︎♍︎♍︎♋︎♈︎♓︎♊︎♈︎♎︎♏︎♏︎♎︎♍︎♏︎♓︎♒︎♏︎♋︎♑︎♓︎♋︎♉︎♊︎♎︎♋︎♉︎♍︎♍︎♊︎♋︎♊︎♌︎♑︎♐︎♐︎♌︎♋︎♋︎♊︎♈︎♋︎♑︎♐︎♓︎♏︎♑︎♋︎♒︎♑︎♋︎♓︎♑︎♉︎♓︎♊︎♒︎♏︎♎︎♐︎♎︎♒︎♓︎♎︎♐︎♋︎♋︎♈︎♎︎♉︎♋︎♉︎♌︎♉︎♏︎♍︎♍︎♏︎♋︎♌︎♌︎♐︎♉︎♐︎♍︎♋︎♓︎♐︎♌︎♍︎♎︎♍︎♋︎♋︎♓︎♌︎♎︎♓︎♉︎♊︎♋︎♊︎♍︎♋︎♐︎♏︎♑︎♋︎♍︎♑︎♍︎♐︎♌︎♌︎♋︎♏︎♊︎♌︎♍︎♈︎♌︎♓︎♏︎♒︎♓︎♎︎♉︎♒︎♐︎♑︎♑︎♍︎♋︎♌︎♏︎♊︎♒︎♐︎♍︎♓︎♐︎♎︎♓︎♈︎♐︎♉︎♈︎♌︎♒︎♈︎♓︎♈︎♈︎♉︎♌︎♊︎♐︎♓︎ |
During the game, I)ruid heard reports of some Players creating elaborate cross-referenced astrology graphs and other complicated methods trying to decode this one. Yes, you were over-thinking it. This was another fairly simple binary encoding method, using astrology symbols to represent 1’s and 0’s. The ciphertext was:
♓︎♐︎♎︎♐︎♓︎♑︎♋︎♈︎♓︎♎︎♈︎♒︎♋︎♈︎♏︎♊︎♓︎♎︎♌︎♓︎♋︎♓︎♉︎♈︎♓︎♌︎♒︎♍︎♐︎♒︎♑︎♋︎♍︎♊︎♌︎♋︎♌︎♍︎♓︎♒︎♍︎♌︎♐︎♌︎♉︎♎︎♉︎♋︎♋︎♈︎♒︎♋︎♌︎♋︎♉︎♌︎♏︎♊︎♒︎♑︎♍︎♊︎♑︎♎︎♋︎♐︎♒︎♒︎♓︎♑︎♌︎♈︎♏︎♏︎♐︎♑︎♏︎♍︎♍︎♉︎♉︎♎︎♒︎♉︎♒︎♌︎♈︎♐︎♏︎♌︎♊︎♉︎♉︎♐︎♊︎♍︎♍︎♑︎♐︎♉︎♑︎♋︎♓︎♍︎♑︎♌︎♈︎♎︎♍︎♎︎♉︎♏︎♋︎♊︎♎︎♉︎♐︎♍︎♏︎♑︎♋︎♈︎♌︎♓︎♍︎♈︎♑︎♊︎♏︎♓︎♐︎♍︎♉︎♑︎♓︎♉︎♓︎♒︎♌︎♐︎♐︎♓︎♏︎♐︎♋︎♊︎♌︎♑︎♏︎♌︎♑︎♈︎♑︎♌︎♌︎♉︎♍︎♍︎♋︎♈︎♓︎♊︎♈︎♎︎♏︎♏︎♎︎♍︎♏︎♓︎♒︎♏︎♋︎♑︎♓︎♋︎♉︎♊︎♎︎♋︎♉︎♍︎♍︎♊︎♋︎♊︎♌︎♑︎♐︎♐︎♌︎♋︎♋︎♊︎♈︎♋︎♑︎♐︎♓︎♏︎♑︎♋︎♒︎♑︎♋︎♓︎♑︎♉︎♓︎♊︎♒︎♏︎♎︎♐︎♎︎♒︎♓︎♎︎♐︎♋︎♋︎♈︎♎︎♉︎♋︎♉︎♌︎♉︎♏︎♍︎♍︎♏︎♋︎♌︎♌︎♐︎♉︎♐︎♍︎♋︎♓︎♐︎♌︎♍︎♎︎♍︎♋︎♋︎♓︎♌︎♎︎♓︎♉︎♊︎♋︎♊︎♍︎♋︎♐︎♏︎♑︎♋︎♍︎♑︎♍︎♐︎♌︎♌︎♋︎♏︎♊︎♌︎♍︎♈︎♌︎♓︎♏︎♒︎♓︎♎︎♉︎♒︎♐︎♑︎♑︎♍︎♋︎♌︎♏︎♊︎♒︎♐︎♍︎♓︎♐︎♎︎♓︎♈︎♐︎♉︎♈︎♌︎♒︎♈︎♓︎♈︎♈︎♉︎♌︎♊︎♐︎♓︎The hint for this one was “Kappa Geminorum”, a binary star system in the Gemini constellation. Hopefully this hint clued Players into this one also being a binary encoding.
Astrology signs each have a “polarity”, with 6 of the 12 signs being “positive” and the other 6 being “negative”. By stepping through the sequence of astrology signs and assigning the “positive” ones to 1 and “negative” ones to 0, you can reconstruct the binary string:
01110001 01110101 01100001 01101100 01101001 01110100 01101001 01100101 01110011 00100000 01101111 01100110 00100000 01110100 01101000 01100101 00100000 01111001 01100101 01100001 01110010 00100000 01100001 01101110 01100100 00100000 01101111 01100110 00100000 01110100 01101000 01100101 00100000 01110011 01100101 01100001 01110011 01101111 01101110Then finally convert that binary to ASCII in the usual way:
qualities of the year and of the seasonEntering “qualities of the year and of the season” would solve this challenge.
A fun property of this particular cipher encoding is that when stepping through a sequence of binary to encode the data, for each 1 or 0 you have six options for astrological signs and can randomly choose any of the six symbols that represent “positive” or “negative”, respectively. This enables this cipher to create a large number of varying ciphertexts that actually all represent the exact same plaintext.
Waltz of the Spider in A Minor
| Hint: | solfege 0 = do = c |
| Location: | 8th plane of hell |
| Challenge: | We found this interesting music on the internet. We think it may contain a message. Asset File |
Zonkism created a fun cipher based on music notes and the solfège scale. Looking at the “Waltz of the spider in A Minor” sheet music you can find a couple of hints to get you started.

The first hint is the time signature of 3/8 which is a fast waltz time signature. The 3 in “3/8” should clue you in to reading the notes as groups of 3. The 8 which would usually indicate 8th notes in the time signature was intended to point you at Base8 (octal) encoding.
If you missed the time signature clue then you could have also derived the 3 and 8 from the title of the sheet music. Waltz hinting at 3 and spider hinting at 8.
If you were stuck we provided hints of “solfege 0 = do = c” and “the 8th plane of hell”. Interpreting the notes using do-re-mi-fa-so-la-ti-do, you would then end up with a string of digits 0-7. Grouping these digits by 3 into larger numbers would then give you the octal values which could then be converted into ASCII, yielding the final answer of:
I got a pocket full of quartersThis is a short verse from the old Pac-Man Fever song that was released in the 80’s.
Multi-step Enigma Cipher
| Hint: | Bletchley Park |
| Location: | behind enemy lines |
| Challenge: | rextg vuiyr ccnhk nahpb dqpjp tvsfb oakdz jomcq vulcx bpbwx tdyrc wxljt bdrzi rsoft fprjc yjnge dhsjj kp KZKESNLEKZYEQVTONRUVMMC2GZLVISTPMNDUU5CWK5SFAYKVJJFVKMKOIJNDANKWKZLWIT3BGFWG4VBSNRBVG3COKZQTEZCOJVCTC3SUKZJE6VDLNRCWEMTEKRKTARTOKNKVER2RNNWEKYKFNRFFERZZNZLFKVSKLIYUEVCRNVWGUVJQJJYVSMTMINQTERSUKFWXQ2DBKVFHSWSINRBWIR2SIRIW4WTKMVKUUM22KVHEGTKXKZYFC3JVNBIVIMBZ |
For the final challenge in ciphers Zonkism wanted to create a multi step challenge while concealing the information that would be used to solve the ciphertext that was given in the challenge description.
The top string is a pretty standard Enigma ciphertext that you may have recognized based on the character spacing and set:
rextg vuiyr ccnhk nahpb dqpjp tvsfb oakdz jomcq vulcx bpbwx tdyrc wxljt bdrzi rsoft fprjc yjnge dhsjj kpThe bottom string is Base32 encoded. The first step was to decode this and then you end up with:
VTI5dVpHVnliV0Z6WTJocGJtVWdPaUJKU1NBZ05VVWdOa1lnT2lCSlNVa2dNME1nTVROTklEb2dTU0FnSURGQklEaElJRG9nVUVJZ1BTQmljU0JqY2lCa2FTQmxhaUJyZHlCdGRDQnZjeUJ3ZUNCMWVpQm5hQT09hopefully you can recognize this as a Base64 string. Base64 decoding it will give you:
U29uZGVybWFzY2hpbmUgOiBJSSAgNUUgNkYgOiBJSUkgM0MgMTNNIDogSSAgIDFBIDhIIDogUEIgPSBicSBjciBkaSBlaiBrdyBtdCBvcyBweCB1eiBnaA==Now that definitely looks like another Base64 string. So let’s Base64 decode that one more time and we get:
Sondermaschine : II 5E 6F : III 3C 13M : I 1A 8H : PB = bq cr di ej kw mt os px uz ghThis string is pointing you towards a specific enigma machine, the Sondermachine. The next set of instructions tell you to configure the rotors and then finally set the PB (plug board) values. Using these values with the original Enigma ciphertext will yield the answer of:
Pwned by TuringScavenger Hunt Track
A returning staple of I)ruid’s challenge games, we definitely wanted to include a basic scavenger hunt. All items needed to be returned to I)ruid himself, who was being tracked around the conference via GPS and was posting images to his Instagram to give clues as to where he was. This had worked well in the past but this year we didn’t seem to have too many Players attempting to return many Scavenger Hunt items. The full list of items was:
| Item | Description | Points |
| 50-cent Piece | A single United States 50-cent piece coin. | 10 |
| Green Sharpie | A green color Sharpie brand marker. | 20 |
| Lime | A whole and uncut lime fruit. | 20 |
| Green Book | A book who’s entire cover, including spine, is the color green. | 20 |
| Green Playing Cards | A green colored deck of playing cards. | 25 |
| Green Hacker T-Shirt | A green colored, size Medium, hacker themed T-shirt. | 25 |
| Green Bacon Pancake | A pancake with bacon baked inside it made from green colored batter. | 25 |
| Green Cloth Napkin | A single green colored cloth napkin. | 30 |
| Green Floppy Disk | A green colored computer floppy disk. | 35 |
| Unique Green Badge | A green badge that I)ruid doesn’t already have. | 90 |
Upon returning a first Scavenger Hunt item, I)ruid would award the Player with the Pinky Ghost puzzle piece:
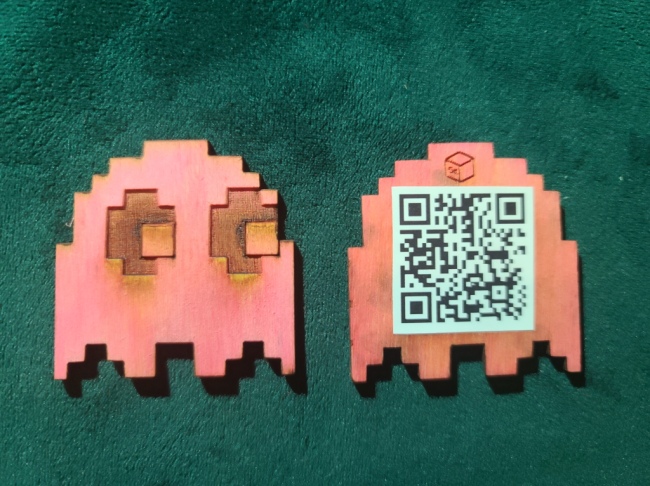
Upon returning a second Scavenger Hunt item, I)ruid would award the Player with the Clyde Ghost puzzle piece:

(More about the Ghost puzzle pieces in the Final Track section)
The most difficult and highest-points item returned was a Green Bacon Pancake, baked by the Player themselves.
Bitcoin Track
Our Bitcoin track of challenges were very similar to many of the “Bitcoin Skills” challenges from our Pyramid Scheme game created for the Bitcoin 2022 conference. This track included challenges meant to test a range of Bitcoin related skills, from some basic chainalysis tasks to more complicated endeavors like decoding Base58, running a Lightning Network node, and cracking the password to an encrypted Bitcoin Core wallet.dat file.
Two notable challenges in this track were contributed by D++ and included a Bitcoin mining simulation challenge and a Lightning Node related challenge.
Manual Mining Challenge
| Hint: | Guess a Valid Nonce |
| Location: | Internet |
| Challenge: | Visit D++’s Mining Simplified webpage. Guess a valid nonce to “mine” a block at the given difficulty target! Any valid nonce will solve this challenge. |
This challenge involved guessing random numbers and performing a hash function to compare against a target difficulty hash, similar to how Bitcoin mining works. You can find the details of how this works at D++’s Mining Simplified webpage, but essentially you could either enter random numbers into the website itself and let it do the calculation and comparison, or you could inspect the code on the site, write your own brute force script, and do the same much, much faster. The challenge’s difficulty value was chosen assuming that most hackers would inspect the code and write a script, thus trying to solve this one by hand using the website was likely not possible in a reasonable timeframe.
PLEBNET Graph
| Hint: | Lightning Node Registration |
| Location: | PLEBNET |
| Challenge: | Visit D++’s PLEBNET Challenge webpage. Join your Lightning Network node to the PLEBNET and return with the password! |
This challenge introduced Players to the PLEBNET, a community of Bitcoin Lightning node operators who have a graph of the network that you can add your own Lightning Node to. The challenge tasked Players with bringing up a Lightning Node if they didn’t already have one and registering it with the PLEBNET. You can find more details about this challenge at D++’s PLEBNET Challenge webpage.
Packet Analysis Track
Our Packet Analysis track of challenges were created and contributed by PrestonZen, and was a bit unique in our game in that this track had an ongoing narrative. In PrestonZen’s own words:
My packet analysis track was made to guide a player from scratch on how to capture and view data transmitting live on networks. It begins with players going to meet up with others at the DEFCON packet capture village then getting more and more involved in packet capturing.
I made a narrative for my challenges to give players context of a situation where packet capturing would be relevant in a real world scenario. This is something I value when doing cyber puzzles myself as the more I can tie my experiences into life-like scenarios, the more I retain the information.
I learned that many of the players were participating in the event remotely from other locations as far away as Greece. This made it difficult for them to meet up and do the in person challenges which I intended for players to experience. Also one of the issues I realized is that if any players plugged into the DEFCON open network and opened up Wireshark they would be bombarded with BILLIONS of packets generated from the DEFCON attendees. I did like how I was able to meet up with attendees/Players at the packet capturing village then show them the basics of how to capture traffic or to get over an obstacle they were having with my challenges.
PrestonZen
You can find a full walk-through of PrestonZen’s Packet Analysis Track over on his blog.
Social Track
Our track of social challenges was designed to get Players out and interacting with each other, various areas of the conference, and a few notable people around the conference. These included tasks like finding another Player with the same hair color, finding someone with a matching badge, or simply meeting some number of other Players and scanning their game profile QR codes. A couple of the notable Social challenges were:
Scan Puzzle’s Backpack
| Hint: | WiFi |
| Location: | On Puzzle’s Back |
| Challenge: | What did Puzzle give you after you scanned her backpack? |
One particular challenge of note was to find Puzzle and scan her backpack. Puzzle is a visual Artist that creates laser-cut wooden sculpture and art. Every year for DEFCON, she creates an art piece backpack with various technical functionality and auctions it off at the end of the conference:

This year’s backpack had remote-controlled multicolor LED strip lighting and had two separate NFC tags embedded in the different DEFCON symbols on the backpack. One NFC acts as her business card and contains the URL to her LinkTree, and the other gave the following message:
Ask me about my ghostPuzzle was being tracked by GPS to make it easier for Players to find her and her backpack. Upon finding her with the backpack, scanning the backpack to find the NFC with the message, and then asking about her ghost, Puzzle would award the Player with the Blinky Ghost puzzle piece:
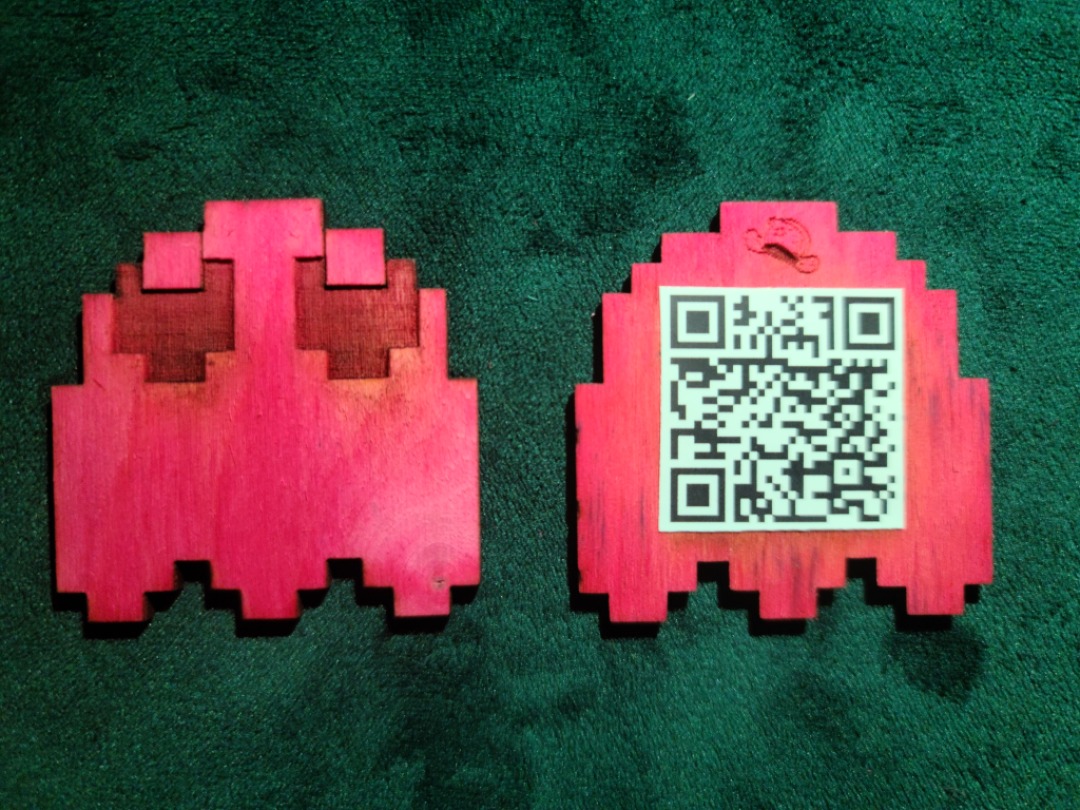
(More about the puzzle pieces in the Final Track section)
Anti-Social
| Hint: | Talk to the AI instead of Real Humans! |
| Location: | The Internet |
| Challenge: | Go talk to the AI until it tells you the password. |
For the anti-social Players, we had a challenge to go talk to the AI until it tells you its password. Built with IBM Watson’s Watson Assistant product, this AI assumed the identity of the ancient Egyptian Pharoah Kufu. Try talking to it about pyramids…
Steganography Track
Our Steganography Track was entirely created and contributed by Zonkism. The rest of this section is written in his own words:
I wanted to provide a series of approachable steganography challenges that were based on basic ways you can hide data in digital files. I didn’t want to include anything that forced the challenger to have to code up a solution. I wanted to take advantage of existing steganography tools that every hacker should know about.
My approach was pretty simple. Each challenge would showcase an interesting way that you could hide data in a file. My goal was to keep it light and engaging and focus on basic steganography techniques. It is always a challenge creating puzzles for DEFCON because attendees show up with a wide spectrum of skill sets. There was nothing new in any of my steganography challenges but hopefully you learned something if you tried them all.
It’s so Meta!
| Hint: | meta’s data |
| Location: | in the file |
| Challenge: | The answer is inside of the image: Asset File |
The first challenge gave you an image of the Meta company’s logo. This was designed to be a warm-up so I tried to leave a lot of clues. The first clue was the Facebook Meta logo indicating the metadata in the file. The second clue was the title “It’s so Meta!”.
To find the answer you simply needed to check the metadata of the file. Examining the metadata would reveal the answer in the Instructions metadata key:
The answer you are seeking is "m3t4d@ta is n0t v3ry s3cre7"Signal2Noise
| Hint: | ENHANCE! |
| Location: | “1840, 1889” |
| Challenge: | What is happening in this image? Can you find the signal in the noise? Asset File |
This challenge was intended to be very approachable and introduce you to the idea of hidden QR codes. To create the challenge I used an image of pure black and white noise. I then created a QR code containing the message and I shrunk it down and altered the transparency of the image to where it could sit inside of the image and read correctly but be difficult to see without really searching for it. It is interesting how a phone will scan the QR code even though you may not be able to notice it right away.
You were given a couple of clues of “ENHANCE!” and then a location of “1840, 1889”. This would point you to the exact location of the QR code via a pixel map of the image.
Scanning the code would give the answer of:
is this something you can see?Pac-maN Gameboard
| Hint: | any strings attached? |
| Location: | in the chunk |
| Challenge: | We like to hide data in all kinds of places. Can you find where we hid the secret in this one? Asset File |
This challenge was created to show how you can hide data inside of a Portable Network Graphics (PNG) image file via custom chunks. Maybe you noticed the capital letters of PNG in the challenge title? This was a clue to focus on PNG steganography tricks. One of the best and easiest tricks is hiding text based data inside of custom chunks. Looking at this image in a hex editor or using strings would reveal the extra chunk data that I added to hide and obscure the answer to the challenge:
$ strings -n 8 hacman_challenges/pacman_game_board.png | grep tEXt
tEXt:S3cr3t tEXt:D4Ta tEXt:1n Th3 tEXt:ChuNkzPutting the text from the four chunks together with spaces as delimiters produces the challenge answer:
S3cr3t D4Ta 1n Th3 ChuNkzNothing to See Here
| Hint: | Unicode |
| Location: | in between the words |
| Challenge: | We love this quote by Frederick Lenz Asset File |
This was simple challenge to introduce the player to using zero width space characters. We gave the player a file that had some text:
”The void is ready to snatch you up like a Pac Man machine and Laskshmi is on vacation. You chant Sring - and you get her answering machine.”
Frederick Lenz
As you may have noticed I really love giving you clues inside of the challenge text. The “void” in the quote should have clued you in to looking at the zero width characters. If not, looking at this text string in a hex editor or other text viewer that shows all characters would have revealed some very strange looking Unicode characters.
Pasting this string into a zero width steganography decoder reveals the answer:
Z3ro_width_ch4rs_H1de_d4taASCII ART
| Hint: | there is a very useful tool for solving this. ya’snow what I mean? |
| Location: | in the void |
| Challenge: | aScii art caN be c0nsidered as a lost art. What Could be hiding heRe? 4 real, there has to be SometHing here right ! Asset File |
I wanted to create a challenge using an off the shelf tool to hide data using white space. The best that I know for this is SNOW. I used some existing ASCII art to hide the extra white space inside of the file. An astute player would have looked at this in a text editor that shows all white space characters and would have known there is more to this ASCII art than meets the eye.
I also gave you some very good clues to get you started down the path. In the challenge description, if you notice the capital letters and the random exclamation mark at the end of the description, they read “SN0WCR4SH!” This is a hint to use snow. This was also a hint at the password for decryption. Some players were confused because they thought they needed to use all caps for the password. The actual password was “sn0wcr4sh!” Another stumbling block happened because not all snow tools handle escaping the exclamation point at the end of the password correctly.
Decoding this using SNOW with the “sn0wcr4sh!” password gives you the answer:
h4cm4n_w1ll_s4ve_th3_dayWeird Tones
| Hint: | be a multi-freq in the sheetz |
| Location: | vocal frequencies |
| Challenge: | We have intercepted this strange audio. Our best guess is this is some weird extraterrestrial techno dance music or or possibly a hidden message. Asset File |
This challenge was a pretty basic DTMF steganography challenge. We gave the player an audio file consisting of DTMF tones in a sequence. Some of the tones were on the right channel of the audio recording in stereo and some were on the left channel.
Transcribing these DTMF tones to numbers and letters (ABCD with *=E and #=F) in the left channel and combining them with the transcribed values on the right channel would give you a hexadecimal string. Converting that hex string to ASCII would give you the answer to the challenge:
t0nes_t0_t3xt!Ghost Bits
| Hint: | not very important |
| Location: | 2^1 |
| Challenge: | Surely this isn’t only a picture of a ghost. Is there a message here? Asset File |
This was a pretty standard Least-Significant Bit (LSB) steganography challenge. A message was hidden in the second bit plane of the image. The easy way to approach this was to download the image and then use a tool like zSteg or stegSolve to discover the secret message embedded in the second bit plane.
You were given a couple of hints if you chose to unlock them. The first hint was “Not very important”. This should have pointed you towards Least Significant Bits. The second hint was the location of 2^1 pointing you to the second bit plane.
Dumping the data on the second bit plane revealed the message:
H1dd3n__d4ta_in_th3_bitzPac-Man Rocks
| Hint: | a specific and very popular tool is useful here. we believe in you. you rock! |
| Location: | inside in the file |
| Challenge: | We really love pacman. We think this wav file would make a great ring tone but the file size looks larger than it should. Asset File |
The Player was presented with an audio file containing a hidden message. This challenge was created using a very popular steganography tool, Steghide.
In order to use the tool you must know the password. As usual, I gave you a big hint in the title “Pac-Man Rocks”. An astute player would have thought of the rockyou wordlist. An additional hint was offered if the player chose to unlock it, “a specific and very popular tool is useful here. we believe in you. you rock!”, again, pointing the player at the rockyou wordlist. Knowing the wordlist to use makes this challenge easier.
At this point it is a brute force exercise to extract the hidden message from the audio file. Using a tool like stegbrute, you can use the rockyou wordlist to brute force the correct password. The password was:
pacmanrulezIf you picked up on the fact that we “love pacman”, you could search the wordlist for all of the words containing “pacman” and create a smaller wordlist from those which made the brute force attempt a little easier.
Pacman Arcade
| Hint: | when you solve this you will be ahead of the curve and on the level |
| Location: | 450 nm |
| Challenge: | Remember spending countless hours playing this at the arcade? We do. Where could we have hid a message in this image? Asset File |
For this challenge we hid data in the alpha channel using a color that was one off from the alpha white color. The easy way to solve this one is to play with the color thresholds and the levels to pop the message out visually. You could also examine the color histogram values and notice there is an anomaly in the blue color plane.
To solve this challenge you needed to adjust either the color levels or thresholds on the blue color plane. The hidden message is revealed at the bottom of the image. The hidden message was:
N0w_Y0u_c4n_see_m3Scavenger Hunt
| Hint: | keep looking deeper. think about typical steg techniques. there is nothing out of the ordinary going on. you need to go 5 hops to get your goal. |
| Location: | 5th level of hell |
| Challenge: | Follow me down this rabbit hole of challenges. You get a file to start with and your job is to find the final message. Just keep following the breadcrumbs. Asset File |
This final difficult challenge was designed to feel like a scavenger hunt where each discovery produced a new breadcrumb to follow until you reached the final secret message.
I tried not to give too many hints on this one because I wanted it to moderately challenge the Player and provide a fun trip through many ways of concealing data in digital files. If a player chose to unlock the hint they would get “keep looking deeper. think about typical steg techniques. there is nothing out of the ordinary going on. you need to go 5 hops to get your goal.” The main hint being that you need to go 5 levels deep to get to your end goal, the secret message.
To begin, the player was given a docx file. Upon trying to open the docx file, MS Word would spit out an error message.
This error message should be the first clue that something is odd about this docx file. The docx file was just a snippet of Pac-Man cheats I pulled off a Wikipedia page. The real message was hidden inside of the docx. A docx is nothing more than a zip file containing XML data. This means you can open a docx file with a zip tool like 7zip and then add your own files and rezip the contents into a new docx file.
Unzipping the Pac-Man cheats docx file revealed a new PNG file called pacman_classic.png. Looking at this PNG in a hex editor reveals there is a zip file attached to the end of the PNG file as well. The file contents of this zip file is a file named Pac-Man Theme (Remix).mp3. You can attach any file to the end of a PNG file and it still opens as an image without any issues.
You can either carve out this MP3 file using a hex editor or extract the file the easy way using foremost or binwalk. Examining this new MP3 file, you will notice that in the metadata, there is an interesting link:
User Defined Text: (Follow Me To) https://www.dropbox.com/s/r7ytyy6p3j16sja/Pac-Man%20Fever-secret.wavDownloading this new WAV file gave you yet another Pac-Man-themed audio file. I hope you listened to this wav file because honestly the Pac-Man Fever song rocks. You might notice while listening to this amazing song that there is some weirdness that happens in the frequency spectrum around the 1 minute mark. Looking at this section of the WAV file in a spectrogram doesn’t show anything until you increase the upper frequency range in the spectrogram. Doing this reveals the amazing ASCII art with the secret message:
I AIN'T AFRAID OF NO GHOSTWord Association Track
Finally, we wanted to include a track of challenges that were not overly technical, and did not require any in-person or social interactions, so we chose word association! Each challenge in this track presented you with a single word and then would accept one or more words as correct answers:
| PROMPT | Valid Association Words | Points |
| DEFCON | 30, conference, forums, groups | 5 |
| WAR | dial, driving, games, walking | 10 |
| BLACK | box, hat, shirt | 20 |
| STACK | smashing, network, technology, protocol | 25 |
| BOOT | loader, strapping, disk | 25 |
| FULL | disclosure, stack, duplex | 35 |
| DIAL | tone, up | 35 |
| HOME | 127.0.0.1, directory | 35 |
| SILICON | graphics, valley | 50 |
| TRUMPET | winsock | 60 |
Final Track
After completing one or more of the parallel subject-matter specific tracks, the Final Track would unlock. These were the final and most difficult challenges before reaching the “end” of the game.
Phantom Rogue Signal
| Hint: | WiFi |
| Location: | Tower |
| Challenge: | Stand up on one leg to elevate yourself to the level of bits in the Atari Pac-Man game to find a group of rogue broadcast signals. Name one of them. |
This challenge hopefully prompted Players into riding the elevators and roaming the halls in the Flamingo Hotel, searching for a suspicious WiFi signal. In one of our Staff’s rooms on the 8th floor of the Lobby Elevators, you could pick up four SSIDs named after the four Pac-Man ghosts, Blinky, Pinky, Inky, and Clyde. Answering with one of these names solved the challenge.
Visible Rogue Signals
| Hint: | Radio |
| Location: | Multiple |
| Challenge: | Locate the visible rogue signals on this map and scan them. What just happened? |
In this challenge, Players were presented with a Google Map with 16 map pins. Going to each location’s map pin, and using the photo hint attached to each map pin, Players hopefully were able to locate a Rogue Signal sticker with an embedded Near-Field Chip (NFC) Tag:

Scanning this NFC Tag with any NFC scanner (included in most modern smart phones) would produce one of sixteen single words from some song lyrics. The song lyrics were:
Never gonna run around and desert you
Rick Astley
Never gonna make you cry
Never gonna say goodbye
What just happened? The Player got Rick-Rolled… Entering any variation of “rick roll” solved this challenge.
Mobile Lockbox
| Hint: | It’s locked. |
| Location: | On the Run! |
| Challenge: | Track down the mobile lockbox. What is inside it? |
This track included a lock-picking challenge as we ended up not including a full lock-picking track this year. Since we did not have a permanent presence anywhere at the conference (maybe the contests area next year?), we went mobile! The Player was tasked with tracking down a person carrying the lockbox around who was being tracked by GPS.

We had a team of people handing off the lockbox to each other and swapping who was being tracked by GPS for people to find. Upon opening the lockbox, Players were presented with the Inky Ghost puzzle piece:

(More about the Ghost puzzle pieces in Pac-Man Collectible Cipher section below)
Crack That WiFi
| Hint: | WEP |
| Location: | Puzzle’s Backpack |
| Challenge: | Crack the WiFi network password for the network coming from Puzzle‘s Backpack. What is the network password? |
Your standard “crack the old WiFi protocol” challenge, we decided to make this one interesting by having the WiFi AP also be mobile, so we stuck it inside Puzzle’s conveniently-powered backpack! Set to use WEP encryption, there are multiple attacks that can be used to crack the network’s password. Entering the network’s password solved this challenge.
Pac-Man Collectible Cipher
| Hint: | 5 Pieces |
| Location: | Other Challenges |
| Challenge: | Collect the wooden puzzle pieces from other Challenge Tracks to assemble the ciphertext and decrypt. Who is the quote attributed to? |
If a Player had managed to make it this far, to the final challenge of the game, we sent them back to other challenge tracks to challenges they may have missed! In order to solve this challenge, the Player needed to collect all five puzzle pieces from solving challenges in other mazes; a Pac-Man and four Ghosts. The challenges that awarded these pieces were:
- Scavenger Hunt – Item 1:
- Scavenger Hunt – Item 2:
- Social Track 7 – Scan Puzzle’s Backpack:
- Final Track 3 – Mobile LockBox:
- Final Track 4 – Crack That WiFi:
Pinky Ghost
Clyde Ghost
Blinky Ghost
Inky Ghost
Pac-Man
The Pac-Man provided an encryption key, and the Ghosts provided four parts of ciphertext that needed to be reassembled in the correct order.

Simply scanning the Pac-Man puzzle piece yielded the key phrase:
Warehouse RaveThere were multiple ways to figure out how to order the Ghosts, including the original order they appear on the Pac-Man arcade game, the direction of their eyes going clockwise or in cardinal direction order (N, E, S, W) as indicated by the compass rose on the Blinky Ghost puzzle piece, or just by brute force (only 4^4 = 24 possible combinations). Also, the final chunk ended in an equal sign (=), usually a give-away for many methods of encoding data. The correctly ordered and reassembled ciphertext was:
CGSMbklx0nPPzc89k271qWeRJoNCE0uZrrKfpLsJAd0zqOIYhaA4EydHKtFhBMq5iBK2XWll4ipPYzmnaIY+OuEudDAIRTb2fHABhayY73Ns6BhGkXa2J7zumEaUGGj5M3kirksNF1/dSsKVWAd+XQv/ijPiLLHIFwnY9RSd0qun+eI9XMjMXLFtAOUVYLqKpoLegiuuTd4=After assembling the ciphertext, the Player needed to determine the type of encryption used. Hints on the Ghost pieces including the RUSSIAN style hat on the RED Ghost “Blinky”, the BLOCK with the number 64 on “Pinky”, and the volcano with MAGMA under it on “Clyde”, hopefully directed Players to the GOST cipher, a Soviet and Russian government standard symmetric key block cipher with a block size of 64 bits, also known as “Magma”.
Using the key information from Pac-Man and the ciphertext from the four Ghosts, the ciphertext could be decrypted to reveal a quote:
If Pac-Man had affected us as kids, we’d all be running around in dark rooms, munching pills and listening to repetitive electronic music.
Marcus Brigstocke
The challenge question asks who the quote is attributed to, so entering “Marcus Brigstocke” would solve this final challenge.
Winning the Game
After completing the final challenge of the game, the Player could progress through a “credits screen” and then return to the Lobby Maze. Completing the Final Track did not end the game, as the winners were determined at the close of the game by points on the Leaderboard, so we wanted to afford Players the opportunity to complete additional challenges to rack up more points even after “winning” the game.
Conclusion
Overall, the game was very well received by Players and many expressed great joy in discovering and playing our game. The Top Ten Players on the Leaderboard at the end of the game at 4pm Pacific on the final day of the conference were all awarded video game themed prizes, chosen by themselves in ranked order from the list of available prizes:
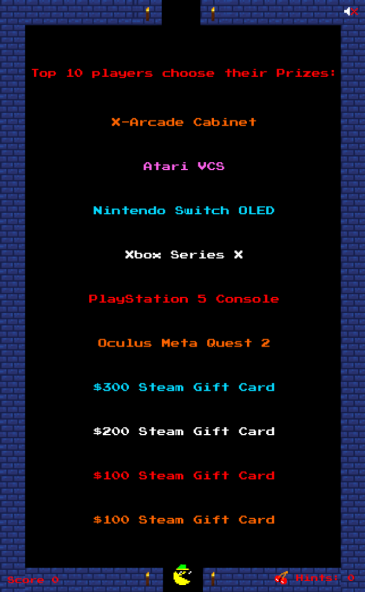
Our Top Ten Players at the end of the game were:

We will definitely be bringing Hac-Man (and friends!) back next year for
DEF CON 31, so prepare thyselves!
Credits
Finally, we’d like to thank all of our amazing challenge content collaborators:

You can find them at the following links:


